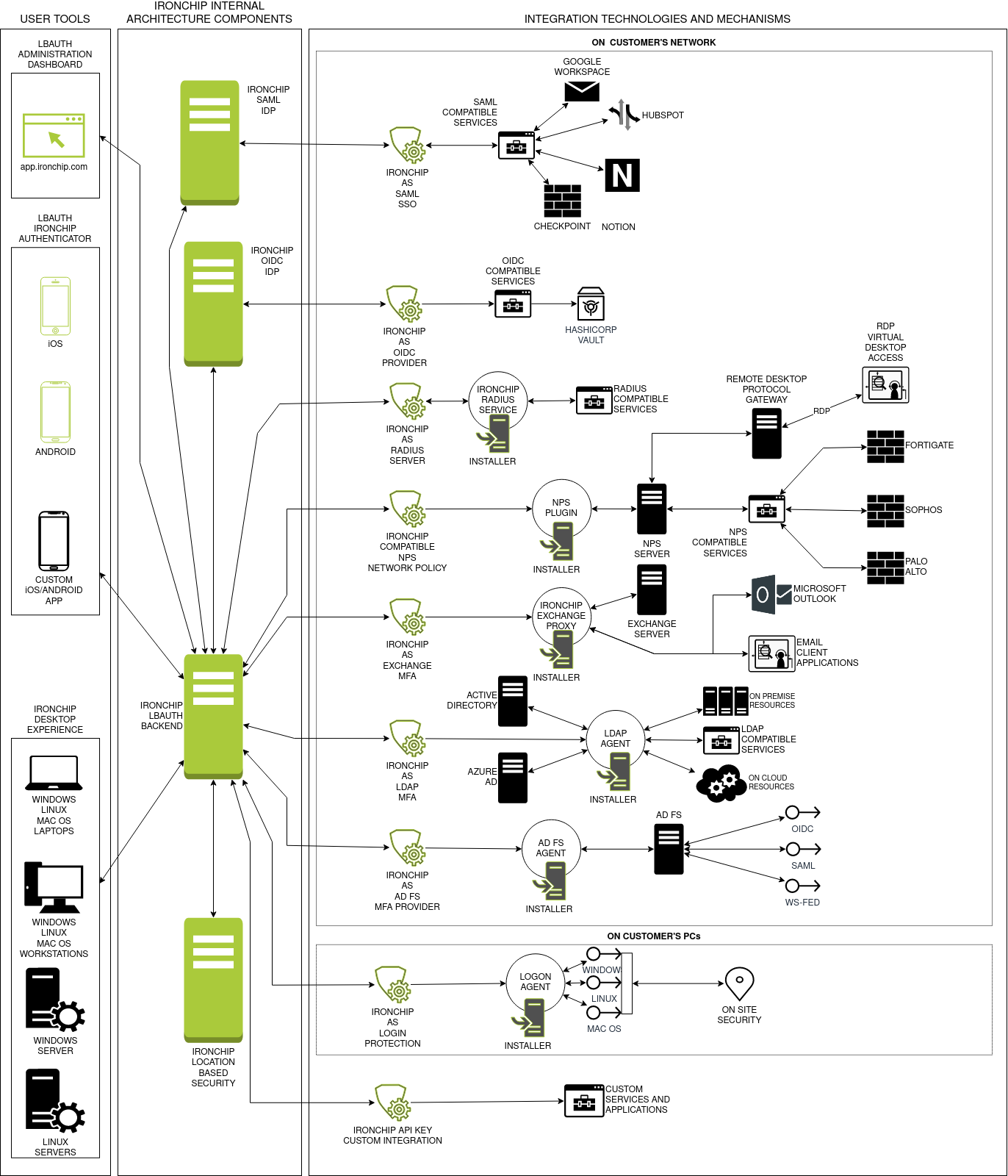
Architecture
User tools
These architectural components are designed to be used by two different kind of users:
- Company manager: the IT technician in charge of managing the policies, users and services connected with Location Based Authentication.
- User: the persons being authenticated using LBAuth.
Authenticator App
Mobile application used by the users of the platform to authorize the accesses to the integrated services in accordance with the access policy established.
Safety based on LBS, uno sin localización y solo con el dispositivo y otro basado en ondas.
Dos modos de funcionamiento, uno con y otro sin localización.
The LBAuth authenticator app is designed to be safe, providing additional safety measures on top of the Location Based Security. It provides biometric mechanisms for local storage unlocking when available making it virtually impossible for an external attacker to clone the device.
It is designed also to be very easy to use and has a user-friendly interface. The Authenticator is meant to be a public application for any user of your company’s services, and to allow all kind of users to authenticate using our application the UX has been taken into account.
By contacting support, it is also possible to obtain a corporate specific application with custom design, color palette, logo and name.
Dashboard
Company manager application to manage the users, integrated services, access policies and integration methods for the platform.
Secciones del dashboard y sus usos, overview.
Ironchip’s LBAuth uses standard protocols for external services integration. This standard protocol allows Ironchip to be integrated with all the popular services such as Microsoft Active Directory, Microsoft Office, Webmails, Adobe products, etc…
The dashboard allows a fine grain control over your corporation access policies, both in terms of which users have access to which services but also in which safezones it is the access possible. This fine grain control allows any IT Administrator full control and accountability over the acceses happening in real-time.
Ironchip provides full support on doubts over the use of the dashboard, providing also multiple resources to enable the easy learning of all the features of the dashboard. These resources include a full walkthrough the platform, action specific tutorials and user documentation.
Integration agents
These agents are the necessary components for the on-site integration between some services depending on specific protocols and LBAuth.
Internal architectural components
These components are internal and transparent to you.
Location Based Security
LBS the business core of ironchip; this component hosts the artificial intelligence responsible of detecting which locations are related and also the distance between these locations.
Location Based Security is a product by itself enabling a company to custom integrate with Ironchip’s security AI. To know more about the possibilities of this product, check (TODO).
LBS is used not only in the context of authentication, it even has lot’s of applications in the world of Fraud detection. Due to this applications on critical tasks, LBS is designed to be resilient, responsive and fast. This requirements translates into a better security and performance for the LBAuth proudct.
Ironchip’s heart is based in both classical deterministic physic-based algorithms and state of the arte AI technologies which enables our algorithm to at the same time be stable, safe, trustworthy and adaptable to new circumpstances.
Location Based Authentication Backend
LBAuth backend exposes the API that implements all the features logic and the communication with the dependant services, i.e. location based security and Dex.
As our backend is the pilar of a security product, one of the main drivers for the development decision making is the security. We have built LBAuth backend around security features such as active monitoring, exclusion of private data from our databases, and ciphered and saltpeppered token and password hashes.
As our business model encompases both big and small businesses, LBAuth Backend is designed with scalability in mind. It is deployed in a dynamic environment which assigns and deassigns capacity based on the current use of the platform.
Lastly, our Backend is stable as it is composed of battle tested technologies, techniques and methodologies and is dependent only to highly available services.
Dex identity provider
Ironchip uses Dex. Dex acts as a portal to other identity providers through “connectors”. This lets dex defer authentication to LDAP servers, SAML providers, or established identity providers like GitHub, Google, and Active Directory. Clients write their authentication logic once to talk to dex, then dex handles the protocols for a given backend.
Dex is an open source project listed on the Cloud native computing foundation (CNCF). This provides a base to consider Dex as an stable and backed project. Dex has an evergrowing community of developers and it is very active among developers.