Boundary
Boundary Configuration
Create an authentication method
Once you have authenticated with the administrator credentials in the Boundary control panel, you can integrate Ironchip as an authentication method. To do so, access the authentication methods in the left menu:
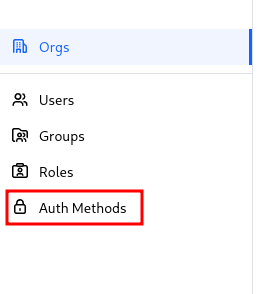
Click New > OIDC
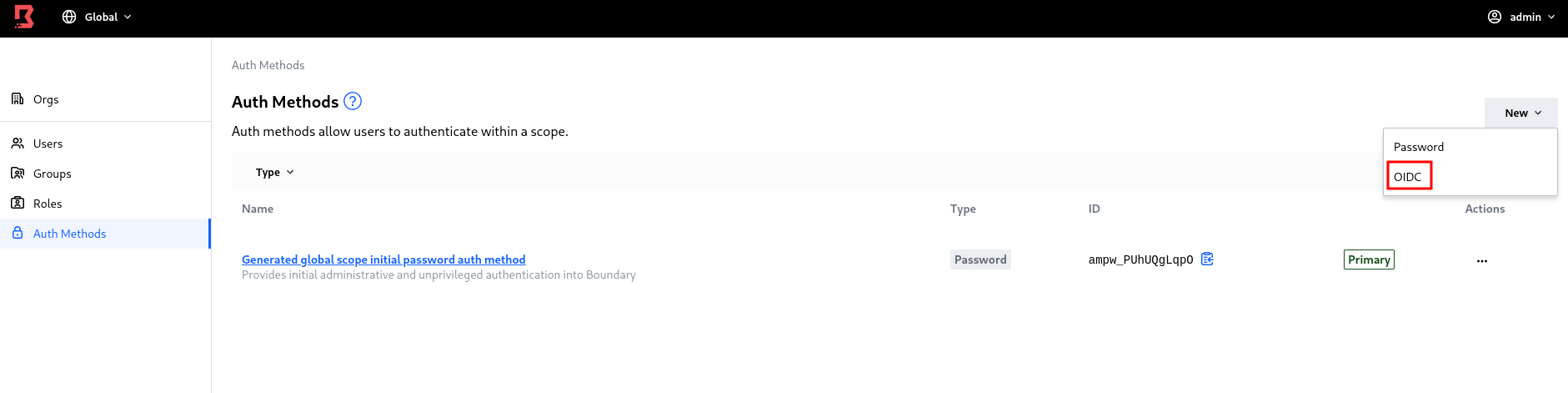
Configure the new auth method in boundary
We will use this data in the Boundary dashboard to complete the integration.
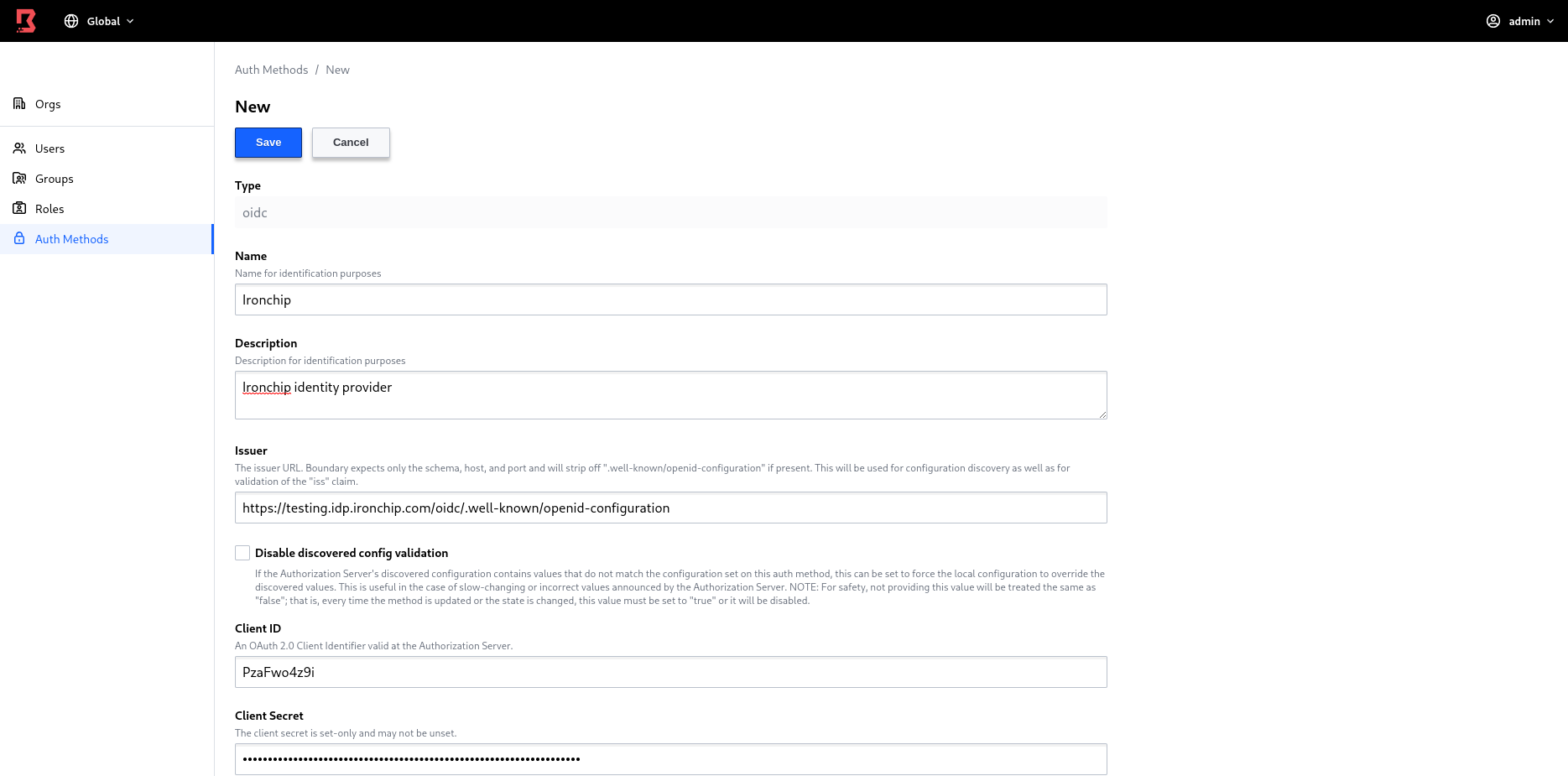
In addition, it is necessary to configure the API URL Prefix, which must correspond to the boundary worker url
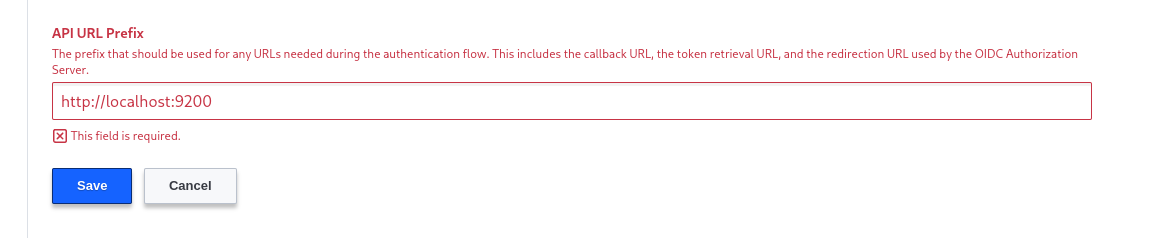
We also need to configure the scopes and attribute mapping.
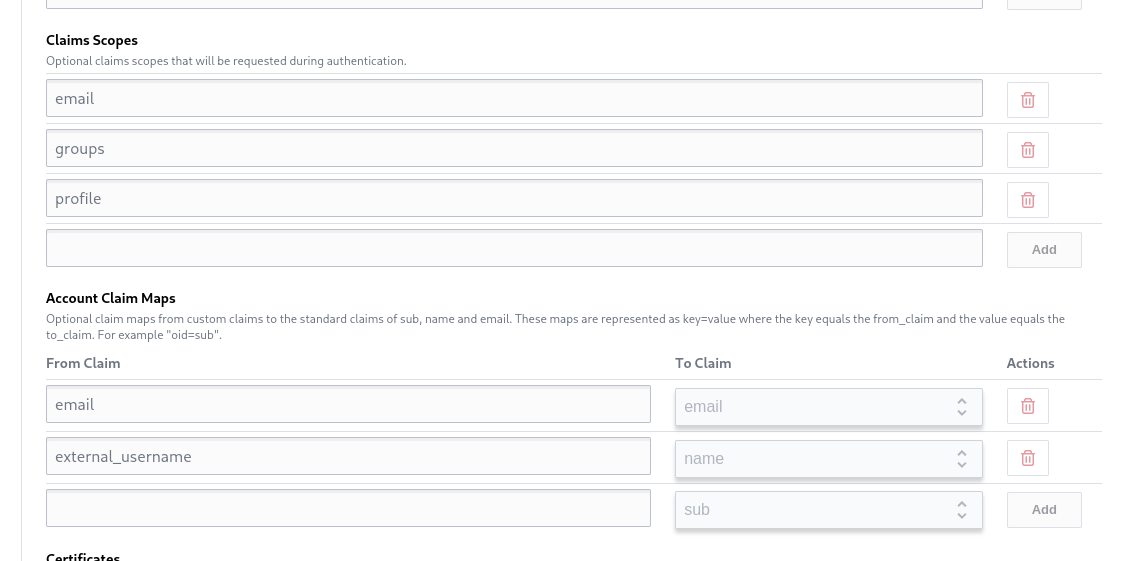
Click save
Enable auth method in Boundary
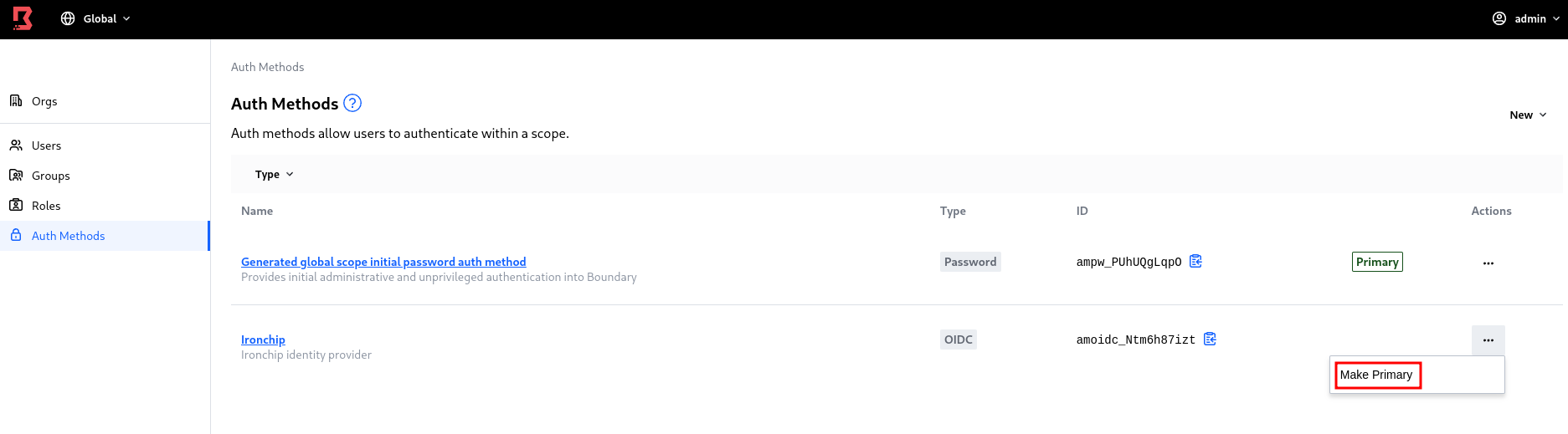
Now in the boundary dashboard, we will make our authentication method the primary authentication method
Enter the authentication method and change it from inactive to public.
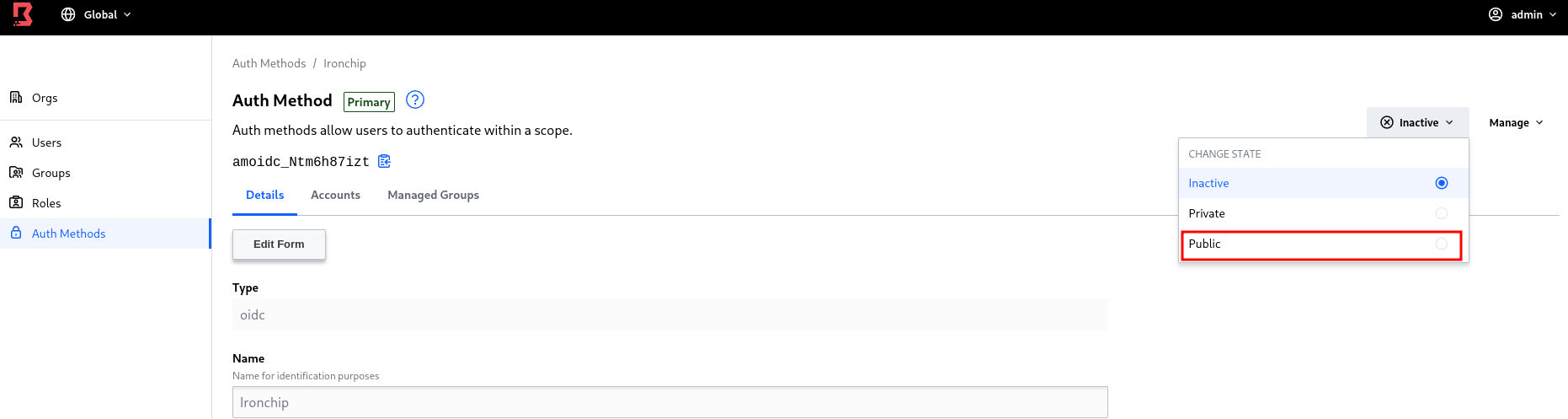
There can be two problems when it comes to going public:
-
The docker machine was not able to resolve the domain ironchip.com, so I added to the /etc/hosts of the machine the domain resolution.
-
When checking the issuer, I put https://idp.ironchip.com/oidc/ and it said that it did not match the issuer of the idp that returned https://idp.ironchip.com/oidc (no trailing slash).
After solving these two problems, it has allowed me to make it public.
To test
We log out of the dashboard, which takes us to the initial login page. Now we will notice that Ironchip is integrated, and offers us to authenticate by pressing just one button. As we have not disabled the other authentication method, we can see both methods on the login screen.
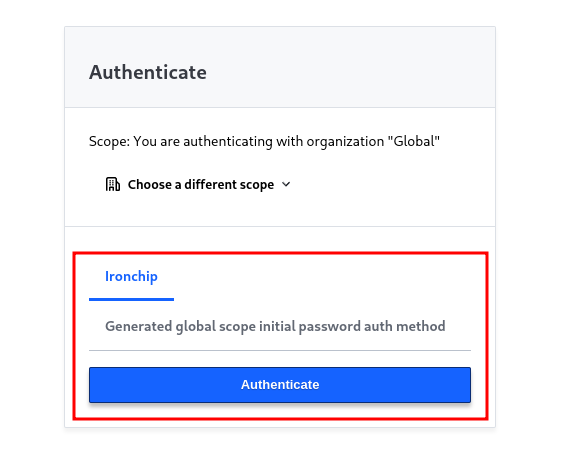
Click on authenticate and we will be redirected to the idp with which we will log in.
Make the ironchip user administrator
Once the first connection is made, it is necessary to log in as the admin user, for this we use the auth with user and pass.
Go to users, enter in the admin user
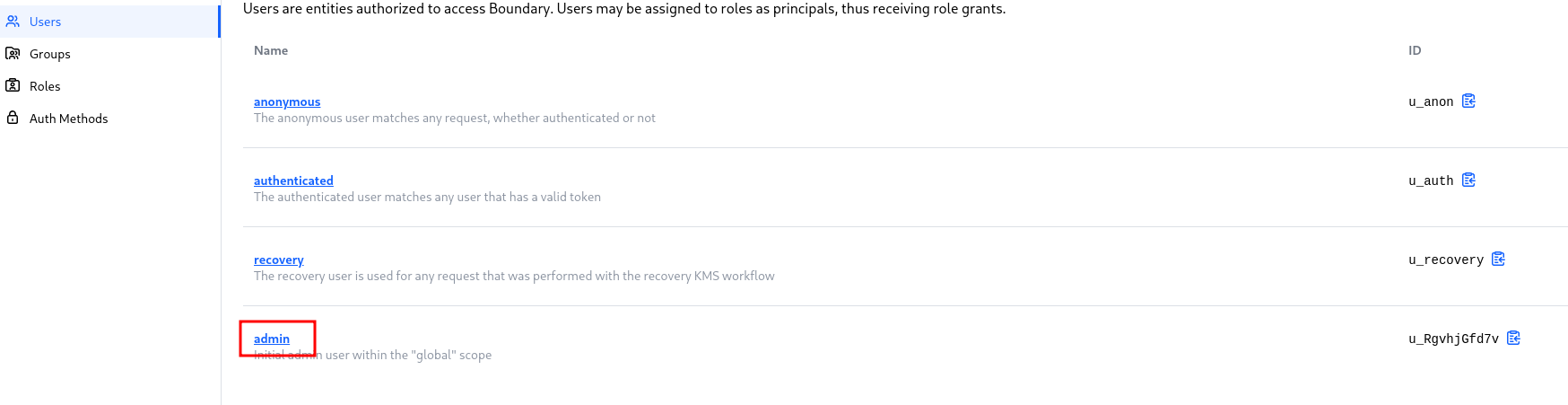
Go to the accounts tab and select add account
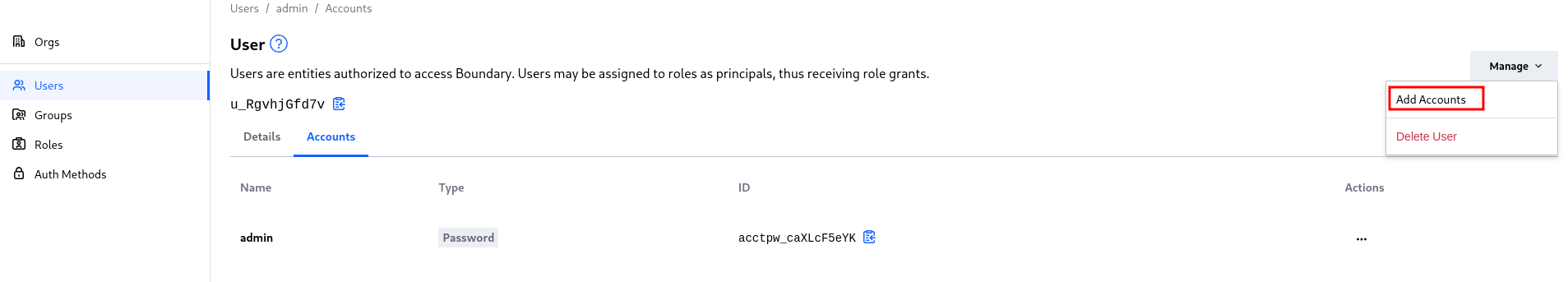
Inside add the oidc account just created
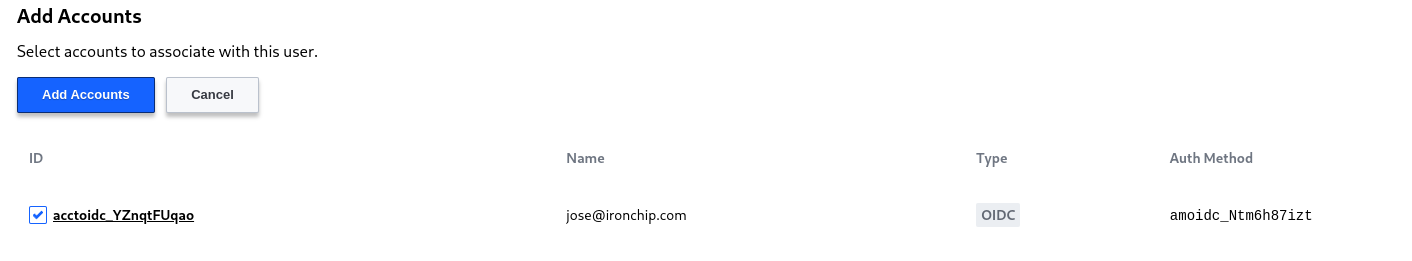
Click on add account and the Ironchip IdP user is already mapped with the administrator user.
We log in by oidc and we will be administrators.